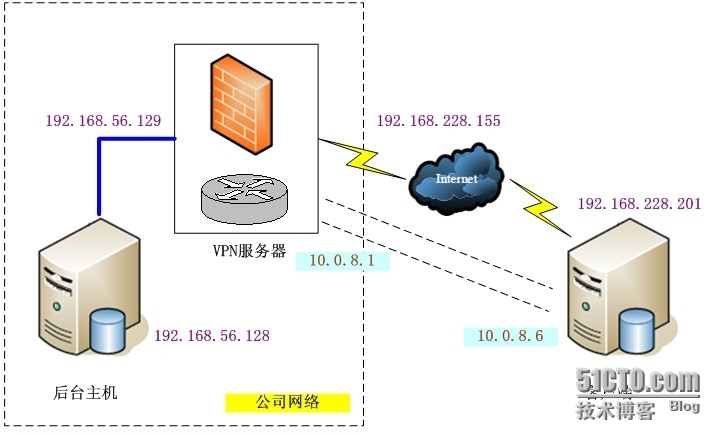
Openvpn在Centos服务器上的完美实现
时间:2014-05-04 23:49 来源:linux.it.net.cn 作者:it
1
2
3
4
5
6
7
8
9
10
11
解压及安装
# tar xvf lzo-2.04.tar.gz
# cd lzo-2.04
# ./configure --prefix=/usr/local/lzo
# make && make install
# cd ../
# tar xvf openvpn-2.1.4.tar.gz
# cd openvpn-2.1.4
# ./configure --prefix=/usr/local/openvpn --with-lzo-headers=/usr/local/lzo/include/ --with-lzo-lib=/usr/local/lzo/lib/ --with-ssl-headers=/usr/include/openssl/ --with-ssl-lib=/usr/lib
# make && make install
# cd ../
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
[root@test1 ~]# mkdir /etc/openvpn
[root@test1 ~]# cp /root/openvpn-2.1.4/easy-rsa/ /etc/openvpn/ -r
[root@test1 ~]# cd /etc/openvpn/easy-rsa/2.0/
[root@test1 2.0]# cat vars |grep -v '^$'|grep -v '^#'
export EASY_RSA="`pwd`" RSA在当前目录
export OPENSSL="openssl"
export PKCS11TOOL="pkcs11-tool"
export GREP="grep"
export KEY_CONFIG=`$EASY_RSA/whichopensslcnf $EASY_RSA`
这个是一个很特别的参数没有“”, openssl的配置文件
export KEY_DIR="$EASY_RSA/keys" 密钥的位置
echo NOTE: If you run ./clean-all, I will be doing a rm -rf on $KEY_DIR
export PKCS11_MODULE_PATH="dummy"
export PKCS11_PIN="dummy"
export KEY_SIZE=1024 密钥的大小长度
export CA_EXPIRE=3650 CA证书的过期时间天数
export KEY_EXPIRE=3650 密钥的时间过期天数
export KEY_COUNTRY="CN" 国家
export KEY_PROVINCE="HB" 省份
export KEY_CITY="WH" 城市
export KEY_ORG="test.com" 组织
export KEY_EMAIL="root@localhost" 邮箱
1
# ./clean-all
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
[root@test1 2.0]# ./build-ca
Generating a 1024 bit RSA private key
..++++++
.....................................................++++++
writing new private key to 'ca.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:CN
State or Province Name (full name) [HB]:HUB
Locality Name (eg, city) [WH]:WH
Organization Name (eg, company) [test.com]:test.com
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) [test.com CA]:test1.test.com
Name []:
Email Address [root@localhost]:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
[root@test1 2.0]# ./build-key-server test1.test.com
Generating a 1024 bit RSA private key
.......................................++++++
..........................++++++
writing new private key to 'test1.test.com.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:CN
State or Province Name (full name) [HB]:HB
Locality Name (eg, city) [WH]:WH
Organization Name (eg, company) [test.com]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) [test1.test.com]:
Name []:
Email Address [root@localhost]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:
Using configuration from /etc/openvpn/easy-rsa/2.0/openssl.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'HB'
localityName :PRINTABLE:'WH'
organizationName :PRINTABLE:'test.com'
commonName :PRINTABLE:'test1.test.com'
emailAddress :IA5STRING:'root@localhost'
Certificate is to be certified until Oct 6 03:30:01 2023 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
[root@test1 2.0]# ./build-key test2.test.com
Generating a 1024 bit RSA private key
............................................................................................................................++++++
......................++++++
writing new private key to 'test2.test.com.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [HB]:
Locality Name (eg, city) [WH]:
Organization Name (eg, company) [test.com]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) [test2.test.com]: 每个client的hostname都不能一样
Name []:
Email Address [root@localhost]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:
Using configuration from /etc/openvpn/easy-rsa/2.0/openssl.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'HB'
localityName :PRINTABLE:'WH'
organizationName :PRINTABLE:'test.com'
commonName :PRINTABLE:'test2.test.com'
emailAddress :IA5STRING:'root@localhost'
Certificate is to be certified until Oct 6 03:36:48 2023 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
1
2
3
4
[root@test1 2.0]# ./build-dh
Generating DH parameters, 1024 bit long safe prime, generator 2
This is going to take a long time
..............+...............+..+..............................................+..+..............+.......+.............
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
[root@test1 2.0]# mkdir /etc/openvpn/easy-rsa/2.0/conf
[root@test1 2.0]# cp /root/openvpn-2.1.4/sample-config-files/server.conf /etc/openvpn/easy-rsa/2.0/conf/
[root@test1 2.0]# cat /etc/openvpn/easy-rsa/2.0/conf/server.conf |grep -v '^$'|grep -v'^;'|grep -v '^#'
port 1194
proto udp
dev tun
ca /etc/openvpn/easy-rsa/2.0/keys/ca.crt
cert /etc/openvpn/easy-rsa/2.0/keys/test1.test.com.crt
key /etc/openvpn/easy-rsa/2.0/keys/test1.test.com.key # This file should be kept secret
dh /etc/openvpn/easy-rsa/2.0/keys/dh1024.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "dhcp-option DNS 192.168.55.25"
push "dhcp-option DNS 8.8.8.8"
client-to-client
keepalive 10 120
comp-lzo
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
log openvpn.log
verb 3
1
2
[root@test1 2.0]# /usr/local/openvpn/sbin/openvpn --config /etc/openvpn/easy-rsa/2.0/conf/server.conf &
[3] 11924
1
2
3
# vim /etc/sysctl.conf
修改以下内容:
net.ipv4.ip_forward = 1
1
2
3
# sysctl –p
# iptables -t nat -A POSTROUTING -o eth0 -s 10.8.0.0/24 -j MASQUERADE
# /etc/init.d/iptables save
TLS: Initial packet from x.x.x.x:x, sid=xxxxxxxx xxxxxxxx
(责任编辑:IT)
TLS: Initial packet from x.x.x.x:x, sid=xxxxxxxx xxxxxxxx |
![21$T61SUE4~XAQFPN]Z@6JV.jpg 100916330.jpg](/uploads/allimg/140504/23494G9E-0.jpg)