CentOS安装配置openvpn使用ldap进行身份认证
时间:2015-07-22 01:36 来源:linux.it.net.cn 作者:IT
一、环境
系统 CentOS 6.4x64最小化安装
IP 192.168.1.8
二、安装openvpn
#基础配置
[root@vpn-ldap ~]# rpm -ivh http://dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm
[root@vpn-ldap ~]# sed -i 's@#b@b@g' /etc/yum.repos.d/epel.repo
[root@vpn-ldap ~]# sed -i 's@mirrorlist@#mirrorlist@g' /etc/yum.repos.d/epel.repo
[root@vpn-ldap ~]# echo "*/10 * * * * /usr/sbin/ntpdate asia.pool.ntp.org &>/dev/null" >/var/spool/cron/root
[root@vpn-ldap ~]# crontab -l
*/10 * * * * /usr/sbin/ntpdate asia.pool.ntp.org &>/dev/null
#安装openvpn
[root@vpn-ldap ~]# yum install openssl openssl-devel lzo openvpn easy-rsa -y
#修改vars文件信息
[root@vpn-ldap ~]# cd /usr/share/easy-rsa/2.0/
[root@vpn-ldap 2.0]# vim vars
#修改下面几项
export KEY_COUNTRY="CN"
export KEY_PROVINCE="GUANGDONG"
export KEY_CITY="GUANGZHOU"
export KEY_ORG="MY COMPANY"
export KEY_EMAIL="lyao@weyee.com"
#重新加载环境变量
[root@vpn-ldap 2.0]# source vars
#清除所有证书和相关文件
[root@vpn-ldap 2.0]# ./clean-all
#生成新的根证书和根秘钥
[root@vpn-ldap 2.0]# ./build-ca
Generating a 2048 bit RSA private key
............................+++
......................................................................................................+++
writing new private key to 'ca.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [GUANGDONG]:
Locality Name (eg, city) [GUANGZHOU]:
Organization Name (eg, company) [MY COMPANY]:
Organizational Unit Name (eg, section) [MyOrganizationalUnit]:
Common Name (eg, your name or your server's hostname) [MY COMPANY CA]:
Name [EasyRSA]:
Email Address [lyao@weyee.com]:
给服务器端生成证书和秘钥
[root@vpn-ldap 2.0]# ./build-key-server server
Generating a 2048 bit RSA private key
....................................................................+++
...........................................+++
writing new private key to 'server.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [GUANGDONG]:
Locality Name (eg, city) [GUANGZHOU]:
Organization Name (eg, company) [MY COMPANY]:
Organizational Unit Name (eg, section) [MyOrganizationalUnit]:
Common Name (eg, your name or your server's hostname) [server]:
Name [EasyRSA]:
Email Address [lyao@weyee.com]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /usr/share/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'GUANGDONG'
localityName :PRINTABLE:'GUANGZHOU'
organizationName :PRINTABLE:'MY COMPANY'
organizationalUnitName:PRINTABLE:'MyOrganizationalUnit'
commonName :PRINTABLE:'server'
name :PRINTABLE:'EasyRSA'
emailAddress :IA5STRING:'lyao@weyee.com'
Certificate is to be certified until Jul 14 13:12:57 2025 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
给vpn客户端创建证书和秘钥,这里我们给win7创建
[root@vpn-ldap 2.0]# ./build-key win7
Generating a 2048 bit RSA private key
.....................+++
......+++
writing new private key to 'win7.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [GUANGDONG]:
Locality Name (eg, city) [GUANGZHOU]:
Organization Name (eg, company) [MY COMPANY]:
Organizational Unit Name (eg, section) [MyOrganizationalUnit]:
Common Name (eg, your name or your server's hostname) [win7]:
Name [EasyRSA]:
Email Address [lyao@weyee.com]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /usr/share/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'GUANGDONG'
localityName :PRINTABLE:'GUANGZHOU'
organizationName :PRINTABLE:'MY COMPANY'
organizationalUnitName:PRINTABLE:'MyOrganizationalUnit'
commonName :PRINTABLE:'win7'
name :PRINTABLE:'EasyRSA'
emailAddress :IA5STRING:'lyao@weyee.com'
Certificate is to be certified until Jul 14 13:13:51 2025 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
生成Diffie Hellman文件
#生成过程可能有点慢,等待一会就好
[root@vpn-ldap 2.0]# ./build-dh
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
...............+.............................................................................................+.......................+...........................................+.................................................................+........................................................+.....+.............................+..........................................................+..............................+..........................................................................................+...........................................................................................+...............................................+.............++*++*
#生成ta.key文件(防DDos攻击、UDP淹没等恶意攻击)
[root@vpn-ldap 2.0]# openvpn --genkey --secret keys/ta.key
#操作完成后查看keys路径下的文件
[root@vpn-ldap 2.0]# pwd
/usr/share/easy-rsa/2.0
[root@vpn-ldap 2.0]# ll keys/
total 88
-rw-r--r-- 1 root root 5604 Jul 17 21:13 01.pem
-rw-r--r-- 1 root root 5481 Jul 17 21:13 02.pem
-rw-r--r-- 1 root root 1801 Jul 17 21:12 ca.crt
-rw------- 1 root root 1704 Jul 17 21:12 ca.key
-rw-r--r-- 1 root root 424 Jul 17 21:14 dh2048.pem
-rw-r--r-- 1 root root 292 Jul 17 21:13 index.txt
-rw-r--r-- 1 root root 21 Jul 17 21:13 index.txt.attr
-rw-r--r-- 1 root root 21 Jul 17 21:13 index.txt.attr.old
-rw-r--r-- 1 root root 147 Jul 17 21:13 index.txt.old
-rw-r--r-- 1 root root 3 Jul 17 21:13 serial
-rw-r--r-- 1 root root 3 Jul 17 21:13 serial.old
-rw-r--r-- 1 root root 5604 Jul 17 21:13 server.crt
-rw-r--r-- 1 root root 1098 Jul 17 21:12 server.csr
-rw------- 1 root root 1708 Jul 17 21:12 server.key
-rw------- 1 root root 636 Jul 17 21:15 ta.key
-rw-r--r-- 1 root root 5481 Jul 17 21:13 win7.crt
-rw-r--r-- 1 root root 1094 Jul 17 21:13 win7.csr
-rw------- 1 root root 1708 Jul 17 21:13 win7.key
创建服务端配置文件
# 在openvpn的配置目录下新建一个keys目录
[root@vpn-ldap ~]# mkdir -p /etc/openvpn/keys
#将openvpn服务端需要用到的证书和秘钥复制到/etc/openvpn/keys目录下
[root@vpn-ldap ~]# cp /usr/share/easy-rsa/2.0/keys/{ca.crt,server.{crt,key},dh2048.pem,ta.key} /etc/openvpn/keys/
[root@vpn-ldap ~]# ll /etc/openvpn/keys/
total 24
-rw-r--r-- 1 root root 1801 Jul 17 21:18 ca.crt
-rw-r--r-- 1 root root 424 Jul 17 21:18 dh2048.pem
-rw-r--r-- 1 root root 5604 Jul 17 21:18 server.crt
-rw------- 1 root root 1708 Jul 17 21:18 server.key
-rw------- 1 root root 636 Jul 17 21:18 ta.key
#复制服务端配置文件到/etc/openvpn
[root@vpn-ldap ~]# cp /usr/share/doc/openvpn-2.3.7/sample/sample-config-files/server.conf /etc/openvpn/
#编辑server.conf文件参数
[root@vpn-ldap ~]# egrep -v "^$|^#|^;" /etc/openvpn/server.conf
#openvpn监听的端口
port 1194
#这里请使用tcp协议,不要使用udp
proto tcp
dev tun
#证书和秘钥的路径,我们放在/etc/openvpn/keys目录下
ca keys/ca.crt
cert keys/server.crt
key keys/server.key # This file should be kept secret
dh keys/dh2048.pem
#这里是默认的虚拟局域网网段,不要和实际网段相同
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
#这里因为我的内网是192.168.10.0/24网段的,所以我修改成192.168.10.0网段
push "route 192.168.10.0 255.255.255.0"
client-to-client
keepalive 10 120
comp-lzo
persist-key
persist-tun
#这是openvpn的日志文件,默认在/etc/openvpn/openvpn.log
status openvpn-status.log
#调试级别
verb 4
启动openvpn服务
#将openvpn添加到开机自启动
[root@vpn-ldap ~]# chkconfig openvpn on
[root@vpn-ldap ~]# service openvpn start
Starting openvpn: [ OK ]
[root@vpn-ldap ~]# netstat -anpt |grep vpn
tcp 0 0 0.0.0.0:1194 0.0.0.0:* LISTEN 1674/openvpn
openVPN 2.3.3 Windows 32位 安装文件:
http://swupdate.openvpn.org/community/releases/openvpn-install-2.3.3-I002-i686.exe
OpenVPN 2.3.3 Windows 64位 安装文件:
http://swupdate.openvpn.org/community/releases/openvpn-install-2.3.3-I002-x86_64.exe
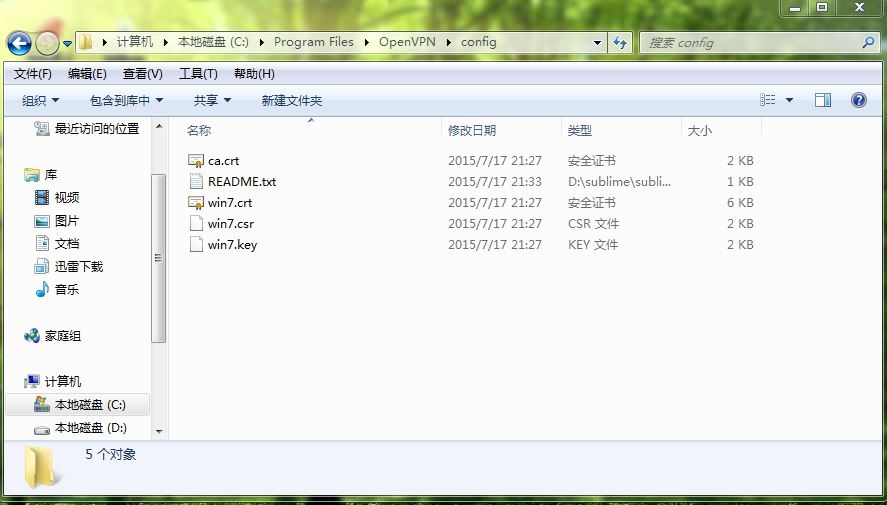
将openvpn服务器上的ca.crt,win7.crt,win7.csr,win7.key,下载到C:\Program Files\OpenVPN\config目录下
[root@vpn-ldap keys]# cp ca.crt win7.crt win7.csr win7.key ~
创建客户端配置文件openvpn.ovpn
client
dev tun
# 改为tcp
proto tcp
remote 192.168.1.8 1194 # OpenVPN服务器的外网IP和端口
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert win7.crt # win7的证书
key win7.key # win7的密钥
ns-cert-type server
# 去掉前面的注释
#tls-auth ta.key 1
comp-lzo
verb 3
连接vpn server
结果正常,可以正常连接到vpn server
查看服务器的日志
[root@vpn-ldap keys]# cat /etc/openvpn/openvpn-status.log
OpenVPN CLIENT LIST
Updated,Fri Jul 17 21:46:37 2015
Common Name,Real Address,Bytes Received,Bytes Sent,Connected Since
win7,192.168.1.100:51915,18131,6421,Fri Jul 17 21:45:08 2015
ROUTING TABLE
Virtual Address,Common Name,Real Address,Last Ref
10.8.0.6,win7,192.168.1.100:51915,Fri Jul 17 21:45:09 2015
GLOBAL STATS
Max bcast/mcast queue length,0
END
三、安装openldap
[root@vpn-ldap ~]# yum install openldap openldap-* -y
[root@vpn-ldap ~]# yum install nscd nss-pam-ldapd nss-* pcre pcre-* -y --skip-broken
配置ldap
[root@vpn-ldap ~]# cd /etc/openldap/
[root@vpn-ldap openldap]# cp /usr/share/openldap-servers/slapd.conf.obsolete slapd.conf
[root@vpn-ldap openldap]# cp slapd.conf slapd.conf_`date +%Y%m%d`.bak
设置ldap管理员密码
[root@vpn-ldap openldap]# slappasswd -s weyee
{SSHA}Zy1IXq8JMGSSOcLnqQ+2wK+f2ms45pg6
[root@vpn-ldap openldap]# slappasswd -s weyee |sed -e "s#{SSHA}#rootpw\t{SSHA}#g" >>/etc/openldap/slapd.conf #密码是weyee
[root@vpn-ldap openldap]# tail -1 /etc/openldap/slapd.conf
rootpw {SSHA}KecOLEH/+7paRfpi+hUYZDblskjDHGXI
修改dc配置
[root@vpn-ldap openldap]# vim /etc/openldap/slapd.conf
#以下参数大概在114行
database bdb #使用bdb数据库
suffix "dc=dev,dc=com" #定义dc,指定搜索的域
rootdn "cn=admin,dc=dev,dc=com" #定义管理员的dn,使用这个dn能登陆openldap
优化ldap配置参数
[root@vpn-ldap openldap]# vim /etc/openldap/slapd.conf
loglevel 296 #定义日志级别
cachesize 1000 #换成条目数
checkpoint 2048 10 #表示内存中达到2048k或者10分钟,执行一次checkpoint,即写入数据文件的操作
配置相关权限
[root@vpn-ldap openldap]# vim /etc/openldap/slapd.conf
#删除默认权限,将下面的内容都删除
database config
access to *
by dn.exact="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage
by * none
# enable server status monitoring (cn=monitor)
database monitor
access to *
by dn.exact="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read
by dn.exact="cn=Manager,dc=my-domain,dc=com" read
by * none
#添加新的权限(这是2.3的权限设置方式)
access to *
by self write
by anonymous auth
by * read
配置syslog记录ldap的服务日志
[root@vpn-ldap openldap]# cp /etc/rsyslog.conf /etc/rsyslog.conf_`date +%Y%m%d`.bak
#往配置文件中增加如下内容
[root@vpn-ldap openldap]# tail -1 /etc/rsyslog.conf
local4.* /var/log/ldap.log
#重启rsyslog服务
[root@vpn-ldap openldap]# /etc/init.d/rsyslog restart
Shutting down system logger: [ OK ]
Starting system logger: [ OK ]
配置ldap数据库路径
#创建数据文件
[root@vpn-ldap openldap]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[root@vpn-ldap openldap]# chown ldap.ldap /var/lib/ldap/DB_CONFIG
[root@vpn-ldap openldap]# chmod 700 /var/lib/ldap/
[root@vpn-ldap openldap]# ll /var/lib/ldap/
total 4
-rw-r--r-- 1 ldap ldap 845 Jul 18 11:02 DB_CONFIG
[root@vpn-ldap openldap]# egrep -v "\#|^$" /var/lib/ldap/DB_CONFIG
set_cachesize 0 268435456 1
set_lg_regionmax 262144
set_lg_bsize 2097152
[root@vpn-ldap openldap]# slaptest -u #检查配置文件是否正常
config file testing succeeded
ldap最后的完整配置如下
[root@vpn-ldap openldap]# egrep -v "^#|^$" /etc/openldap/slapd.conf
include /etc/openldap/schema/corba.schema
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/duaconf.schema
include /etc/openldap/schema/dyngroup.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/java.schema
include /etc/openldap/schema/misc.schema
include /etc/openldap/schema/nis.schema
include /etc/openldap/schema/openldap.schema
include /etc/openldap/schema/ppolicy.schema
include /etc/openldap/schema/collective.schema
allow bind_v2
pidfile /var/run/openldap/slapd.pid
argsfile /var/run/openldap/slapd.args
TLSCACertificatePath /etc/openldap/certs
TLSCertificateFile "\"OpenLDAP Server\""
TLSCertificateKeyFile /etc/openldap/certs/password
access to *
by self write
by anonymous auth
by * read
database bdb
suffix "dc=dev,dc=com"
rootdn "cn=admin,dc=dev,dc=com"
directory /var/lib/ldap
index objectClass eq,pres
index ou,cn,mail,surname,givenname eq,pres,sub
index uidNumber,gidNumber,loginShell eq,pres
index uid,memberUid eq,pres,sub
index nisMapName,nisMapEntry eq,pres,sub
rootpw {SSHA}KecOLEH/+7paRfpi+hUYZDblskjDHGXI
loglevel 296
cachesize 1000
checkpoint 2048 10
启动ldap服务
[root@vpn-ldap ~]# /etc/init.d/slapd start
Starting slapd: [ OK ]
[root@vpn-ldap ~]# netstat -tunlp |grep slapd
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 1652/slapd
tcp 0 0 :::389 :::* LISTEN 1652/slapd
[root@vpn-ldap ~]# ps aux | grep slapd
ldap 1652 0.1 1.7 494664 17632 ? Ssl 11:04 0:00 /usr/sbin/slapd -h ldap:/// ldapi:/// -u ldap
root 1660 0.0 0.0 103248 868 pts/0 S+ 11:05 0:00 grep slapd
#添加到开机自启动
[root@vpn-ldap ~]# chkconfig slapd on
#查看日志文件
[root@vpn-ldap ~]# tail /var/log/ldap.log
Jul 18 11:04:58 vpn-ldap slapd[1651]: @(#) $OpenLDAP: slapd 2.4.39 (Oct 15 2014 09:51:43) $#012#011mockbuild@c6b8.bsys.dev.centos.org:/builddir/build/BUILD/openldap-2.4.39/openldap-2.4.39/build-servers/servers/slapd
查询一下ldap的内容
[root@vpn-ldap ~]# ldapsearch -LLL -w weyee -x -H ldap://192.168.1.8 -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=*)"
ldap_bind: Invalid credentials (49) #这里有报错
#解决如下,删除默认2.4的配置文件,重新生成2.3的配置文件
[root@vpn-ldap ~]# rm -rf /etc/openldap/slapd.d/*
[root@vpn-ldap ~]# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/
55a9c327 bdb_monitor_db_open: monitoring disabled; configure monitor database to enable
config file testing succeeded
[root@vpn-ldap ~]# ll /etc/openldap/slapd.d/
total 8
drwxr-x--- 3 root root 4096 Jul 18 11:08 cn=config
-rw------- 1 root root 1302 Jul 18 11:08 cn=config.ldif
#重启服务
[root@vpn-ldap ~]# /etc/init.d/slapd restart
Stopping slapd: [ OK ]
Checking configuration files for slapd: [FAILED]
55a9c34c ldif_read_file: Permission denied for "/etc/openldap/slapd.d/cn=config.ldif"
slaptest: bad configuration file!
[root@vpn-ldap ~]# chown -R ldap.ldap /etc/openldap/slapd.d
[root@vpn-ldap ~]# /etc/init.d/slapd restart
Stopping slapd: [FAILED]
Starting slapd: [ OK ]
[root@vpn-ldap ~]# netstat -tunlp | grep slapd
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 1732/slapd
tcp 0 0 :::389 :::* LISTEN 1732/slapd
#再重新查询ldap内容
[root@vpn-ldap ~]# ldapsearch -LLL -w weyee -x -H ldap://192.168.1.8 -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=*)"
No such object (32) #ldap中还没有任何数据
安装migrationtools
[root@vpn-ldap ~]# yum install migrationtools -y
#编辑migrationtool的配置文件/usr/share/migrationtools/migrate_common.ph
[root@vpn-ldap ~]# vim /usr/share/migrationtools/migrate_common.ph
# Default DNS domain
$DEFAULT_MAIL_DOMAIN = "dev.com";
# Default base
$DEFAULT_BASE = "dc=dev,dc=com";
#下面利用pl脚本将/etc/passwd 和/etc/shadow生成LDAP能读懂的文件格式,保存在/tmp/下
[root@vpn-ldap ~]# /usr/share/migrationtools/migrate_base.pl >/tmp/base.ldif
[root@vpn-ldap ~]# /usr/share/migrationtools/migrate_passwd.pl /etc/passwd >/tmp/passwd.ldif
下面就要把这二个文件导入到LDAP,这样LDAP的数据库里就有了我们想要的用户
#导入base
[root@vpn-ldap ~]# ldapadd -x -D "cn=admin,dc=dev,dc=com" -W -f /tmp/base.ldif
Enter LDAP Password:
adding new entry "dc=dev,dc=com"
adding new entry "ou=Hosts,dc=dev,dc=com"
adding new entry "ou=Rpc,dc=dev,dc=com"
adding new entry "ou=Services,dc=dev,dc=com"
adding new entry "nisMapName=netgroup.byuser,dc=dev,dc=com"
adding new entry "ou=Mounts,dc=dev,dc=com"
adding new entry "ou=Networks,dc=dev,dc=com"
adding new entry "ou=People,dc=dev,dc=com"
adding new entry "ou=Group,dc=dev,dc=com"
adding new entry "ou=Netgroup,dc=dev,dc=com"
adding new entry "ou=Protocols,dc=dev,dc=com"
adding new entry "ou=Aliases,dc=dev,dc=com"
adding new entry "nisMapName=netgroup.byhost,dc=dev,dc=com"
#导入passwd
[root@vpn-ldap ~]# ldapadd -x -D "cn=admin,dc=dev,dc=com" -W -f /tmp/passwd.ldif
Enter LDAP Password:
adding new entry "uid=root,ou=People,dc=dev,dc=com"
adding new entry "uid=bin,ou=People,dc=dev,dc=com"
adding new entry "uid=daemon,ou=People,dc=dev,dc=com"
adding new entry "uid=adm,ou=People,dc=dev,dc=com"
adding new entry "uid=lp,ou=People,dc=dev,dc=com"
adding new entry "uid=sync,ou=People,dc=dev,dc=com"
adding new entry "uid=shutdown,ou=People,dc=dev,dc=com"
adding new entry "uid=halt,ou=People,dc=dev,dc=com"
adding new entry "uid=mail,ou=People,dc=dev,dc=com"
adding new entry "uid=uucp,ou=People,dc=dev,dc=com"
adding new entry "uid=operator,ou=People,dc=dev,dc=com"
adding new entry "uid=games,ou=People,dc=dev,dc=com"
adding new entry "uid=gopher,ou=People,dc=dev,dc=com"
adding new entry "uid=ftp,ou=People,dc=dev,dc=com"
adding new entry "uid=nobody,ou=People,dc=dev,dc=com"
adding new entry "uid=dbus,ou=People,dc=dev,dc=com"
adding new entry "uid=vcsa,ou=People,dc=dev,dc=com"
adding new entry "uid=abrt,ou=People,dc=dev,dc=com"
adding new entry "uid=haldaemon,ou=People,dc=dev,dc=com"
adding new entry "uid=ntp,ou=People,dc=dev,dc=com"
adding new entry "uid=saslauth,ou=People,dc=dev,dc=com"
adding new entry "uid=postfix,ou=People,dc=dev,dc=com"
adding new entry "uid=sshd,ou=People,dc=dev,dc=com"
adding new entry "uid=tcpdump,ou=People,dc=dev,dc=com"
adding new entry "uid=openvpn,ou=People,dc=dev,dc=com"
adding new entry "uid=ldap,ou=People,dc=dev,dc=com"
adding new entry "uid=nscd,ou=People,dc=dev,dc=com"
adding new entry "uid=avahi,ou=People,dc=dev,dc=com"
adding new entry "uid=nslcd,ou=People,dc=dev,dc=com"
再次查询ldap的内容
[root@vpn-ldap ~]# ldapsearch -LLL -w weyee -x -H ldap://192.168.1.8 -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=root)"
dn: uid=root,ou=People,dc=dev,dc=com
uid: root
cn: root
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:: e2NyeXB0fSQxJGhhaGFoYSR0VWhYaXFQSHNncFJFODBsNGZpQjkw
shadowLastChange: 16633
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 0
gidNumber: 0
homeDirectory: /root
gecos: root
在ldap中新建一个用户user1,密码是user1,过程略
查询结果如下
[root@vpn-ldap ~]# id user1
id: user1: No such user
[root@vpn-ldap ~]# ldapsearch -LLL -w weyee -x -H ldap://192.168.1.8 -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=user1)"
dn: uid=user1,ou=People,dc=dev,dc=com
objectClass: posixAccount
objectClass: top
objectClass: inetOrgPerson
gidNumber: 0
givenName: user1
sn: user1
uid: user1
homeDirectory: /home/user1
cn: user1
uidNumber: 15546
userPassword:: e1NIQX1zOXFuZTB3RXFWVWJoNEhRTVpIK0NZOHlYbWM9
#结果说明user1只有ldap才有
在/etc/openvpn下创建2个文件
[root@vpn-ldap ~]# cat /etc/openvpn/authfile.conf #openvpn授权文件
user1 #这个用户是ldap中的用户
[root@vpn-ldap ~]# cat /etc/openvpn/user.conf
user1 #ldap中的用户
user1 #用户的密码
创建python脚本
[root@vpn-ldap openvpn]# cat check_credit.py
#!/usr/bin/python
import sys
import os
import logging
import ldap
# settings for ldap
ldap_uri = "ldap://dev.com:389"
ldap_starttls = True
ldap_dn = "uid=%s,ou=People,dc=dev,dc=com"
# settings for logging
log_filename = "/tmp/check_ldap.log"
log_format = "%(asctime)s %(levelname)s %(message)s"
log_level = logging.DEBUG
# settings for authorization
auth_filename = "/etc/openvpn/authfile.conf"
def get_users(fpath):
fp = open(fpath, "rb")
lines = fp.readlines()
fp.close()
users = {}
for line in lines:
line = line.strip()
if len(line) <= 0 or line.startswith('#'):
continue
users[line] = True
return users
def get_credits(fpath):
fp = open(fpath, "rb")
lines = fp.readlines()
fp.close()
assert len(lines)>=2, "invalid credit file"
username = lines[0].strip()
password = lines[1].strip()
return (username, password)
def check_credits(username, password):
passed = False
ldap.set_option(ldap.OPT_PROTOCOL_VERSION, ldap.VERSION3)
l = ldap.initialize(ldap_uri)
if ldap_starttls:
l.start_tls_s()
try:
l.simple_bind_s(ldap_dn % (username,), password)
passed = True
except ldap.INVALID_CREDENTIALS, e:
logging.error("username,'%s' /password,'%s' failed verifying" % (username,password))
l.unbind()
return passed
def main(argv):
credit_fpath = argv[1]
(username,password) = get_credits(credit_fpath)
if len(username) <= 0 or len(password) <= 0:
logging.error("invalid creadits for user '%s'" % username)
return 1
logging.info("user '%s',password '%s' request logining" % (username,password))
if check_credits(username, password):
users = get_users(auth_filename)
if not username in users:
logging.error("user '%s' not authorized to access" % username)
return 1
logging.info("access of user '%s' granted" % username)
return 0
else:
logging.error("access of user '%s' denied" % username)
return 1
if __name__ == "__main__":
logging.basicConfig(format=log_format,filename=log_filename,level=log_level)
if len(sys.argv) != 2:
logging.fatal("usage: %s <credit-file>" % sys.argv[0])
sys.exit(1)
rcode = 1
try:
rcode = main(sys.argv)
except Exception, e:
logging.fatal("exception happened: %s" % str(e))
rcode = 1
sys.exit(rcode)
执行脚本,并查看日志
[root@vpn-ldap openvpn]# python check_credit.py user.conf
[root@vpn-ldap openvpn]# cat /tmp/check_ldap.log
2015-07-18 13:41:29,246 INFO user 'user1',password 'user1' request logining
2015-07-18 13:41:29,830 CRITICAL exception happened: {'info': 'TLS error -5938:Encountered end of file', 'desc': 'Connect error'}
解决如下:
[root@vpn-ldap openvpn]# cd /etc/openldap/certs/
[root@vpn-ldap certs]# ls
cert8.db key3.db password secmod.db
#创建私钥
[root@vpn-ldap certs]# openssl genrsa -out ldap.key 2014
Generating RSA private key, 2014 bit long modulus
.....+++
......+++
e is 65537 (0x10001)
#生成签名请求
[root@www certs]# openssl req -new -key ldap.key -out ldap.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:
State or Province Name (full name) []:
Locality Name (eg, city) [Default City]:
Organization Name (eg, company) [Default Company Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:www.dev.com
Email Address []:lyao@weyee.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
#公钥
[root@www certs]# openssl x509 -req -days 1095 -in ldap.csr -signkey ldap.key -out ldap.crt
Signature ok
subject=/C=XX/L=Default City/O=Default Company Ltd/CN=www.dev.com/emailAddress=lyao@weyee.com
Getting Private key
[root@www certs]# ll
total 112
-rw-r--r-- 1 root root 65536 Jul 17 22:09 cert8.db
-rw-r--r-- 1 root root 16384 Jul 17 22:09 key3.db
-rw-r--r-- 1 root root 1229 Jul 18 13:46 ldap.crt
-rw-r--r-- 1 root root 1009 Jul 18 13:45 ldap.csr
-rw-r--r-- 1 root root 1639 Jul 18 13:43 ldap.key
-r-------- 1 root root 45 Jul 17 22:09 password
-rw-r--r-- 1 root root 16384 Jul 17 22:09 secmod.db
#修改权限
[root@www openldap]# chmod 700 certs/
[root@www openldap]# chown ldap.ldap certs/ -R
#修改配置文件,添加证书路径
[root@www openldap]# vim /etc/openldap/ldap.conf
TLS_CACERTDIR /etc/openldap/certs
#修改openldap配置文件
[root@www openldap]# vim /etc/openldap/slapd.conf
TLSCertificateFile /etc/openldap/certs/ldap.crt
TLSCertificateKeyFile /etc/openldap/certs/ldap.key
#重启slapd服务
[root@www openldap]# slaptest -u
config file testing succeeded
[root@www openldap]# /etc/init.d/slapd restart
Stopping slapd: [ OK ]
Starting slapd: [ OK ]
[root@www openldap]# netstat -tunlp |grep slapd
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 5757/slapd
tcp 0 0 :::389 :::* LISTEN 5757/slapd
(责任编辑:IT)
一、环境 系统 CentOS 6.4x64最小化安装 IP 192.168.1.8 二、安装openvpn
给服务器端生成证书和秘钥
给vpn客户端创建证书和秘钥,这里我们给win7创建
生成Diffie Hellman文件
创建服务端配置文件
启动openvpn服务
openVPN 2.3.3 Windows 32位 安装文件: http://swupdate.openvpn.org/community/releases/openvpn-install-2.3.3-I002-i686.exe OpenVPN 2.3.3 Windows 64位 安装文件: http://swupdate.openvpn.org/community/releases/openvpn-install-2.3.3-I002-x86_64.exe 将openvpn服务器上的ca.crt,win7.crt,win7.csr,win7.key,下载到C:\Program Files\OpenVPN\config目录下
创建客户端配置文件openvpn.ovpn
连接vpn server
结果正常,可以正常连接到vpn server 查看服务器的日志
三、安装openldap
配置ldap
设置ldap管理员密码
修改dc配置
优化ldap配置参数
配置相关权限
配置syslog记录ldap的服务日志
配置ldap数据库路径
ldap最后的完整配置如下
启动ldap服务
查询一下ldap的内容
安装migrationtools
下面就要把这二个文件导入到LDAP,这样LDAP的数据库里就有了我们想要的用户
再次查询ldap的内容
在ldap中新建一个用户user1,密码是user1,过程略 查询结果如下
在/etc/openvpn下创建2个文件
创建python脚本
执行脚本,并查看日志
解决如下:
(责任编辑:IT) |