一、软件说明
IPsec 是 虚拟私密网络(VPN) 的一种,用于在服务器和客户端之间建立加密隧道并传输敏感数据之用。它由两个阶段组成,第一阶段(Phrase 1, ph1),交换密钥建立连接,使用互联网密钥交换(ike)协议; 第二阶段(Phrase 2, ph2),连接建立后对数据进行加密传输,使用封装安全载荷(esp)协议。参考:维基百科 IPsec 词条。
其中,第一阶段和第二阶段可以使用不同的加密方法(cipher suites)。甚至,第一阶段 ike 协议的第一版(ikev1)有两种模式,主力模式(main mode)和积极模式(aggressive mode),主力模式进行六次加密握手,而积极模式并不加密,以实现快速建立连接的目的。
第一阶段的 ike 协议有两个版本(ikev1/ikev2),不同的开源/闭源软件实现的版本均不同,不同的设备实现的版本也不同。再联系到第一阶段/第二阶段使用的各种不同加密方法,使得 IPsec 的配置有点黑魔法的性质,要么完全懂,通吃; 要么完全不懂,照抄。
二、设备操作系统规格
这里主要介绍了设备/操作系统使用的 ike 版本及其特殊要求。
Linux
命令行客户端就是 strongswan 本身,因此完美兼容,支持 ikev1/ikev2 和所有加密方法的连接。因此如果用户只使用 Linux 命令行客户端,不使用各种移动设备也不使用 Windows,那么完全没有那么多事。
但 Linux 的图形界面客户端 NetworkManager-strongswan 目前只支持 ikev2 连接,必须使用证书或 EAP (各种加密方法都支持,包括微软的 MSCHAPv2)进行认证,不支持纯密码(PSK)认证。这并不是 strongswan 的错误,或者技术不行(开源总是走在技术最前沿的,毕竟命令行是支持的),而仅仅是体现一种选择:ikev1 被 strongswan 项目认为是该淘汰的协议,而 PSK 加密被认为是非常不安全的。参考 strongswan 维基 NetworkManager 词条。
Android
Android 和 Linux 不一样,只支持 ikev1。其它方面和 Linux 一样,甚至有好多种 IPsec VPN 配置模式可供选择。
iOS/Mac OS X
它们声明使用的 IPsec 客户端为 Cisco,实际为自己修改的 racoon。它只支持 ike 协议的第一版即 ikev1,可以使用证书或纯密码(PSK)认证,但必须辅之 xauth 用户名/密码认证。
该修改版的 racoon 会优先使用不加密的积极模式,而积极模式是 strongSwan 所不支持的。所以要使用主力模式。
iOS 6 还有一个「衔尾」故障:它在第一阶段握手时会把数据包拆分成小块(fragmentation),然后「加密」发送。然而这种加密仅仅是声明的,其实并未加密,这就导致 strongSwan 及其它标准服务器端/Cisco 设备无法解密。另外 ikev1 的 fragmentation 插件是闭源的。开源服务器端无法对这些小块进行重组。参考:Cisco VPN stop working after upgrading to IOS 6
所以产生了一种权宜之计,就是使用小证书(小于 1024,默认一般为 2048),来达到不拆包的目的。但是 Mac OS X 10.7 的更新却对这种方式进行了封杀,学习微软加入了证书验证,小证书直接拒绝。
所幸 strongswan 5.0.2 已经完成了 fragmentation 的开源实现和对 iOS 那个声明加密其实未加密故障的处理:IKE message fragmentation (cisco) + IOS 6.0 Hack for encrypted flaged ike fragmentation packets,该链接中也能找到 strongswan 4 的补丁。
Windows
微软的差劲只比 iOS 好一点。好处在于它支持了 ikev2,但是只在 Windows 7 以后支持,Vista 之前依然使用 ikev1,坏处在于它的 ikev2 支持非常诡异,指定了 Diffie Hellman group(DH,迪菲-赫尔曼密钥交换组)必须是 modp1024。这是非常少见理论上不应该由系统管理员操心的加密选项:
在 strongswan 中,定义第一阶段(ike)和第二阶段(esp)加密方法的语法是:
ike/esp=encryption-integrity[-dhgroup][-esnmode]
第一阶段/第二阶段=加密方法-健壮性认证方法 (后面两项可选)[-DH 组] [-扩展序列号支持模式(RFC4304)]
参考:IKEv2CipherSuites
Windows 定义了一个可选的选项,导致了我们必须去定义整个第一阶段的加密方法。这样被破解的可能性就提高了。
其次在于它的 rekey(重连)。IPsec 的认证是有时效的,超过时间会重新认证。这种 CHILD_SA 认证可由服务器发出,也可由客户端发出,一般是由服务器发出。但是 Windows 7 的 ikev2 的表现是,如果你在路由器(NAT)后,收到这种请求会把微软内部的通知代码发出去,代码为 12345, 经过 strongswan 项目侦错后发现这个代码的意思是 ERROR_IPSEC_IKE_INVALID_SITUATION。但是处理不了,它不是 IPsec 标准协议定义过的错误。
于是有两种权宜之计:
一种是让 Windows 7 来主动 rekey。Windows 7 rekey 的时间大约是 58 分 46 秒,所以要配置服务器 rekey 时间比它长。但是效果非常不好。因为 rekey 是由三个变量控制的,key 的生命周期,key 的边际时间(生命周期前多久进行 rekey),和边际时间误差(rekeyfuzz),误差是不可控的。参考:ExpiryRekey。
即使能控制 strongswan 这边,Windows 依然是「大约」; 即使两边都能控制,假设服务器延后一秒 rekey,理论上如果连接持续时间足够长,依然能够撞车:58x60+46 次 rekey 后即 146 天后撞车,连一年都没有,在 Linux 服务器对 Windows 服务器这种使用实例中就明显不符合要求。
所以目前只能使用后一种方法即完全禁用服务器端 rekey。
最后,它的 EAP 认证也非常糟糕。MSCHAPv2 的 eap 身份不是 ikev2 身份(ikev2 身份一般是 EAP 用户名),所以必须在服务器端显式定义 eap_identity 来使用 Windows 7 的 eap 身份。
三、软件的安装
软件的安装很方便,这里我们使用epel仓库里面的yum安装
# yum install strongswan
一条命令就安装好了,下面来查看安装了哪些文件
# rpm -ql strongswan
这里我就不展示有哪些内容,下面来看看我们主要使用的配置文件
# rpm -qc strongswan
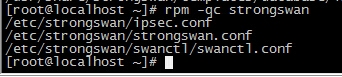
其中/etc/strongswan/ipsec.conf是主要的配置文件,我们也主要对他进行配置
开启转发
# echo 1 > /proc/sys/net/ipv4/ip_forward
四、软件的配置
1、证书的创建,我这里不再进行演示,大家可以下面的文章
http://wangzan18.blog.51cto.com/8021085/1676529
假设证书都已经创建好了,我们把证书放到下面的目录
2、编辑ipsec.conf
# vim /etc/strongswan/ipsec.conf
config setup
uniqueids=never
conn iOS_cert
keyexchange=ikev1
fragmentation=yes
left=%defaultroute
leftauth=pubkey
leftsubnet=0.0.0.0/0
leftcert=server.crt
right=%any
rightauth=pubkey
rightauth2=xauth
rightsourceip=10.31.2.0/24
rightcert=client.crt
auto=add
conn android_xauth_psk
keyexchange=ikev1
left=%defaultroute
leftauth=psk
leftsubnet=0.0.0.0/0
right=%any
rightauth=psk
rightauth2=xauth
rightsourceip=10.31.2.0/24
auto=add
conn networkmanager-strongswan
keyexchange=ikev2
left=%defaultroute
leftauth=pubkey
leftsubnet=0.0.0.0/0
leftcert=server.cert.pem
right=%any
rightauth=pubkey
rightsourceip=10.31.2.0/24
rightcert=client.crt
auto=add
|
3、ipsec.conf配置文件的详解
其中 config setup 只能出现一次,而 conn <连接名称> 可以有很多个。这里的名称不是预定义的,可以随意写,只要你能识别就行,主要用来定义一种连接,就是为了让你在日志里好找。
新版 strongswan 里 config setup 的内容不如旧版的多,许多旧版必须有的选项都被作废了。比如:
1.plutostart 新版所有的 ike 协议都由原来 ikev2 的 daemon:charon 接管。根本就没有 pluto 了。
2.nat_traversal 新版所有的 ike 协议都是可以穿越路由器(NAT)的。
3.virtual_private 定义服务器的局域网 IP 地址。现在被魔术字 0.0.0.0/0 取代了。
4.pfs 完美向前保密,用于 rekey 时。意思是你现在的密钥互换过程如果被攻破了,会不会对已经互换过的密钥产生影响。以前一般设置成 no 来适用于 iOS 这种客户端会以积极模式发出非加密的 rekey 请求的情况。现在这个选项完全没作用了。第一阶段永远是完美向前保密的,第二阶段(esp)如果指定了 DH 组那么也是完美向前保密的,但是默认加密方法就已经指定了 DH 组。所以该选项永远为 yes。
而另外旧版和新版都有的选项也都定义了默认值,比如:
1.strictpolicy 是否一定需要证书吊销列表(CRL)的 URL。默认就是 no。
2.charonstart 是否启动 ikev2 的 daemon。这是旧版加入的,因为那个时候的主力是 pluto。现在默认就是 yes,你改成 no 那你连原先 pluto 的连接都无法连接,因为 ike 协议的实现全被 charon 接管了。
所以 config setup 基本上占位就行了。这里我们修改了 uniqueids 的值来实现多设备同时在线。
而 conn 最主要要理解左右的概念。其实左右是可以不分的,它们只是用来表示一个连接的两端。只是在如果你定义的不够全面时,左侧会默认被认为是本机(你的 VPS),右侧默认为他机(你的笔记本),即以左为尊。
1.left/right 是左右 id。它们用来识别服务器/客户端,可以是证书的判别名(DN),比如 "C=CN, O=strongSwan, CN=strongSwan CA",也可以是 IP 地址,也可以是 EAP 的用户名,还可以是魔术字 %any,表示什么都行。只是在 5.0.0 之前,为本机这边定义 %any 的话,ikev1 连接即 keyexchange=ikev1 的连接是识别不了,所以要改成 %defaultroute 表示自己从 ifconfig 里取 IP。为了和 right 的 %any 区分开,我们使用这种方法。所以说到最后这两个选项似乎没有什么用。但它们是必须的。
2.leftauth/rightauth 这是最重要的改动。新版主要是作废了之前的 authby 和 xauth=server/client 选项而都改用这种方法。因此使得 ikev1 也能够出现混血认证(左右两边认证的方法不同)了。参数主要有 pubkey 表示用证书,psk 表示用密码,eap 表示用扩展验证协议。
3.leftauth2/rightauth2 是为了应对旧版很常见的 authby=xauthpsk/xauthrsasig 的。现在 xauth 只能写在这里。而 psk 对应 leftauth/rightauth 里的 PSK 方法,rsasig 则对应 pubkey 方法。
4.leftsubnet 最重要的,引入了魔术字 0.0.0.0/0。如果你在右侧为客户端分配虚拟 IP 地址的话,那表示你之后要做 iptables 转发,那么左边就必须是用魔术字。
5.leftcert/rightcert 就是指定证书名字。
6.rightsourceip 为客户端分配的虚拟 IP 段。
7.auto 定义 strongswan 启动时该连接的行为。start 是启动; route 是添加路由表,有数据通过就启动; add 是添加连接类型但不启动; ignore 是当它不存在。默认是 ignore。看起来似乎是 route 比较好,但问题是我们服务器端不能预分配虚拟 IP,所以服务器端一般用的都是 add。而客户端文本配置可以选择 start。
另外说下旧版的 xauth=server/client 的问题。它表示在服务器端还是在客户端执行 xauth 认证。而在新版中主要通过左右方向来体现。比如你在服务器端执行认证,那认证请求是由客户端发出的,所以要写 rightauth2=xauth。如果在客户端执行认证,那认证请求是服务器发出的,所以要写 leftauth2=xauth。
另外网上很常见的一个配置选项是 leftfirewall=yes。这是完全错误的。看上去它的唯一作用是定义你的服务器是不是在防火墙后面,但实际上它是作为 ipsec_updown 脚本的参数被开发出来,是表明你的本机 subnet 是不是用 iptables 转发/伪装出来的。如果是的话,就调用 left/rightupdown 定义的路径下的脚本,脚本的作用是对通过 ipsec 连接的数据包进行 iptables 豁免。
之所以说它是错到离谱的(虽然没有产生影响),因为这些人完全就不懂,有公网 IP 的服务器的 subnet 很少是伪装的。另外必须写了脚本该选项才有意义,没看过一个定义了这个选项的人写过脚本。还有,leftsubnet=0.0.0.0/0 通过魔术字把 subnet 定义为了 any,你根本没法写脚本啊。所以我们这里完全就不用。
至于某类型连接,主要是根据设备规格定义的,一些特殊选项的解释如下:
1.fragmentation=yes 开启对 iOS 拆包的重组支持。
2.ike=aes256-sha1-modp1024! Windows 指定的第一阶段加密方法。
3.rekey=no 服务器对 Windows 发出 rekey 请求会断开连接。
4.rightsendcert=never 因为这是一个混血连接。服务器对自己的身份进行认证时使用的是证书,而服务器对客户端的认证使用的只是 eap-mschapv2。如果不设置的话默认是 ifasked,意思是如果服务器向客户端请求证书,客户端就会给它,但客户端给不出,连接就会断。这里设置为客户端永远不给,实际上的意思其实是服务器不要向客户端请求证书。
5.eap_identity=%any 使用 Windows 的 eap 身份。不然会出现”no eap key found for host <rightid>“错误。
4、ipsec.secrets配置
这个文件默认是没有的,我自己来进行创建
# vim /etc/strongswan/ipsec.secrets
: RSA server.pem
: PSK "myPSKkey"
: XAUTH "myXAUTHPass"
[用户名] %any : EAP "[密码]"
|
将上面的myPSKkey单词更改为你需要的PSK认证方式的密钥;
将上面的myXAUTHPass单词更改为你需要的XAUTH认证方式的密码,该认证方式的用户名是随意的;
将上面的[用户名]改为自己想要的登录名,[密码]改为自己想要的密码([]符号去掉),可以添加多行,得到多个用户,这即是使用IKEv2的用户名+密码认证方式的登录凭据.
: PSK "PSK password" 相当于:%any %any : PSK "PSK password"
遵循:“主机 对等点 : 方法 <本机证书/协议密码> <本机证书密码>”的格式。以 :为分界,分别从左到右填充,除了各类密码缺失以 null 补位,其它都用 %any 补位(密码怎么可能是 %any)。
5、strongswan.conf配置
# vim /etc/strongswan/strongswan.conf
charon {
load_modular = yes
duplicheck.enable = no
compress = yes
plugins {
include strongswan.d/charon/*.conf
}
dns1 = 114.114.114.114
nbns1 = 114.114.114.114
}
include strongswan.d/*.conf
|
dns可以改为你想使用的dns,可以添加两个dns1 dns2
五、服务的启动
# service strongswan start
然后我们就可以使用手机进行连接了
六、客户端的设置
iOS
把 CA 证书和之前做好的 pkcs12(.p12)发邮件给自己。在 iOS 上收邮件,导入两者。然后新建 IPSec VPN:
Android
IPSec Xauth PSK
主要还是:
然后登入时还是用 XAUTH 前后的那两个做用户名密码。
"strongSwan VPN Client" for Android 4.0 (ICS)+
这是官方自己出的客户端,Google Play 里就有。
把之前做好的 pkcs12 发邮件给自己。实际上 pkcs12 里就包含了 CA 证书,iOS 是有 bug 才必须明确要求导入 CA 证书(鄙视之)。Android 不用。直接在 GMail 里点击就会提示你导入。
然后打开官方客户端,新建方案:
Windows的客户端我还是建议使用pptp或者l2tp openvpn
七、问题调试
如果没有特殊需要,服务器端的日志就足够检测出绝大多数问题的来源。
日志阅读技巧
strongswan 的 charon daemon 启动后,会初始化并加载之前你定义好的 conn,这部分 log 是没有必要去读的。当然在你配置有问题时可能就有必要了,但当配置有问题的时候,service strongswan start会失败,strongswan status就会指出你配置问题所在的行号(=。=)...
服务器端调试
/var/log/strongswan-charon.log 文件
需要在/etc/strongswan/strongswan.d/charon-logging.conf里面开启调试日志功能
iOS 调试
越狱安装 iFile。编辑 /etc/racoon/racoon.conf 文件,找到 #log debug; 字段,改成:
log debug;
path logfile "/var/log/racoon.log";
保存。
Android 调试
打开「终端模拟器」,输入 su,会弹出超级用户,允许。
cd /storage/sdcard0
logcat -f ./log.txt
然后用 Airdroid 等工具把 SD 卡中的 log.txt 传到电脑上,打开搜索 VPN 即可。
八、总结
经过我测试得出的结论,我目前只测试了IOS 8还有安卓手机小米Note,都是使用的xauth认证,没有使用证书,我的小米Note是可以连接的上,但是页面加载有问题,查看日志他是使用的android_xauth_psk这个连接,也没有找到问题的原因,同样的配置用IOS连接,因为我们使用的是IOS自带的IPSec VPN连接,也没有使用证书,参数和安卓的连接一样,因为没有使用证书,识别的也是android_xauth_psk这个连接,但是访问都是一切正常的。
更多请大家关注http://www.wzlinux.com 或者http://www.wzlinux.com:45/
如果有什么问题欢迎大家和我一起探讨。
(责任编辑:IT) |
