Iphone/Ipad/Mac OSX IPSEC VPN with Strongswan 5 on Centos/RHEL 6
时间:2015-12-09 23:36 来源:www.it.net.cn 作者:IT
Introduction
This howto describes setting up an IPSEC VPN for use with the Iphone, Ipad and Mac OSX VPN clients on Centos/RHEL 6. I am using the 5.x branch of Strongswan which is now the mainline actively maintained branch. At the time of writing the 5.x EPEL package was only available in the testing repo.
The configuration should work both with NAT and without NAT on both sides, if you are NATing on the server side make sure your forward UDP 500 and 4500 to the machine running strongswan.
This howto uses example.org and 192.168.1.0/24 and 192.168.2.0/24 networks for illustration purposes, you need to change these to suit your own setup.
Install
To access the EPEL packages you need to enable the EPEL repo. You are then able to install the strongswan package.
yum install --enablerepo=epel-testing strongswan
Create the required configuration directories
mkdir -p /etc/strongswan/ipsec.d/{aacerts,acerts,cacerts,certs,crls,ocspcerts,private}
Configuration
Create a CA
For RSA authentication you need to setup a CA which will issue the certificates to be used by the server and the clients.
cd /etc/pki/tls/misc
./CA -newca
echo 00 > /etc/pki/CA/crlnumber
openssl ca -gencrl -out /etc/pki/CA/crl.pem
Install to strongswan directories
ln -s /etc/pki/CA/cacert.pem /etc/strongswan/ipsec.d/cacerts/
ln -s /etc/pki/CA/crl.pem /etc/strongswan/ipsec.d/crls/
Create the server certificate
Apple clients require that the servers certificate subjectAltName attribute contain either the server IP address or server DNS name. To ensure the server certificate contains the subjectAltName attribute edit the openssl.cnf and set it under the [ usr_cert ] section
For DNS name set it to
subjectAltName=DNS:vpn.example.org
For IP address set it to
subjectAltName=IP:192.168.1.1
Now generate and sign the server certitifcate
./CA -newreq
./CA -sign
Install to strongswan directories.
mv newcert.pem /etc/strongswan/ipsec.d/certs/vpn.example.org.pem
mv newkey.pem /etc/strongswan/ipsec.d/private/vpn.example.org.key
Add the private key password to /etc/strongswan/ipsec.secrets
: RSA vpn.example.org.key "p4ssw0rd"
Create the client certificate
This is the certificate that will be used by you VPN clients ie Ipad/Iphone, edit the openssl.cnf and comment out the subjectAltName attribute setting.
Now generate and sign the client certificate, do this for all the clients you expect to use.
./CA -newreq
./CA -sign
openssl pkcs12 -export -in ipad.example.org.pem -inkey ipad.example.org.key \
-certfile /etc/pki/CA/cacert.pem -out ipad.p12
You now need to import the CA certificate and the client p12 certificate on to the device. You need to download the Iphone configuration utility and use it to import the certificates to your device.
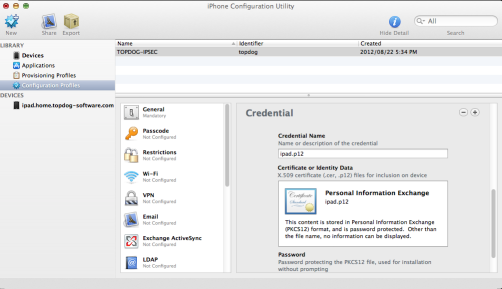
Add the username and password to /etc/strongswan/ipsec.secrets
andrew : XAUTH "5tr0ngp4ss0rd"
Create strongswan configuration
Edit /etc/strongswan/ipsec.conf with the following content.
config setup
conn %default
ikelifetime=60m
keylife=20m
rekeymargin=3m
keyingtries=1
keyexchange=ikev1
left=%defaultroute
leftsubnet=192.168.1.0/24
auto=add
conn rw-xauth leftcert=vpn.example.org.pem leftid=@vpn.example.org leftauth=pubkey leftfirewall=no right=%any rightauth=pubkey rightauth2=xauth rightsourceip=192.168.2.0/24
The above setup assumes the network behind the vpn is 192.168.1.0/24 and virtual IP addresses will be assigned to VPN clients from the 192.168.2.0/24 network block.
Add iptables rules
Edit your /etc/sysconfig/iptables and add the following rules
-A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
-A FORWARD -m state --state NEW -s 192.168.2.0/24 -j ACCEPT
-A FORWARD -m state --state NEW -s 192.168.1.0/24 -j ACCEPT
Enable packet forwarding
If your system is not setup for packet forwarding enable it.
echo 1 > /proc/sys/net/ipv4/ip_forward
Edit /etc/sysctl.conf and set
net.ipv4.ip_forward = 1
Testing
Start strongswan.
service strongswan start
Check /var/log/messages and /var/log/secure for any errors.
Ipad configuration
-
Launch Settings then select General > Network > VPN > Add VPN Configuration
-
Toggle VPN type to IPSec
Set the Fields
Description Strongswan-IPSEC
Server vpn.example.org
Account andrew
Password 5tr0ngp4ss0rd
Use Certificate ON
Certificate ipad.example.org
A VPN connection should now be possible by toggling VPN to ON under Settings > VPN .
http://www.topdog.za.net/2012/08/23/iphone-ipad-mac-osx-ipsec-vpn-with-strongswan-5-on-centos-rhel-6/?utm_source=tuicool&utm_medium=referral
(责任编辑:IT)
IntroductionThis howto describes setting up an IPSEC VPN for use with the Iphone, Ipad and Mac OSX VPN clients on Centos/RHEL 6. I am using the 5.x branch of Strongswan which is now the mainline actively maintained branch. At the time of writing the 5.x EPEL package was only available in the testing repo. The configuration should work both with NAT and without NAT on both sides, if you are NATing on the server side make sure your forward UDP 500 and 4500 to the machine running strongswan. This howto uses example.org and 192.168.1.0/24 and 192.168.2.0/24 networks for illustration purposes, you need to change these to suit your own setup. InstallTo access the EPEL packages you need to enable the EPEL repo. You are then able to install the strongswan package.
Create the required configuration directories
ConfigurationCreate a CAFor RSA authentication you need to setup a CA which will issue the certificates to be used by the server and the clients.
Install to strongswan directories
Create the server certificateApple clients require that the servers certificate subjectAltName attribute contain either the server IP address or server DNS name. To ensure the server certificate contains the subjectAltName attribute edit the openssl.cnf and set it under the [ usr_cert ] section For DNS name set it to
subjectAltName=DNS:vpn.example.org
For IP address set it to
subjectAltName=IP:192.168.1.1
Now generate and sign the server certitifcate
Install to strongswan directories.
Add the private key password to /etc/strongswan/ipsec.secrets : RSA vpn.example.org.key "p4ssw0rd" Create the client certificateThis is the certificate that will be used by you VPN clients ie Ipad/Iphone, edit the openssl.cnf and comment out the subjectAltName attribute setting. Now generate and sign the client certificate, do this for all the clients you expect to use.
You now need to import the CA certificate and the client p12 certificate on to the device. You need to download the Iphone configuration utility and use it to import the certificates to your device.
Add the username and password to /etc/strongswan/ipsec.secrets andrew : XAUTH "5tr0ngp4ss0rd" Create strongswan configurationEdit /etc/strongswan/ipsec.conf with the following content. config setup conn %default ikelifetime=60m keylife=20m rekeymargin=3m keyingtries=1 keyexchange=ikev1 left=%defaultroute leftsubnet=192.168.1.0/24 auto=add conn rw-xauth leftcert=vpn.example.org.pem leftid=@vpn.example.org leftauth=pubkey leftfirewall=no right=%any rightauth=pubkey rightauth2=xauth rightsourceip=192.168.2.0/24 The above setup assumes the network behind the vpn is 192.168.1.0/24 and virtual IP addresses will be assigned to VPN clients from the 192.168.2.0/24 network block. Add iptables rulesEdit your /etc/sysconfig/iptables and add the following rules -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT -A FORWARD -m state --state NEW -s 192.168.2.0/24 -j ACCEPT -A FORWARD -m state --state NEW -s 192.168.1.0/24 -j ACCEPT Enable packet forwardingIf your system is not setup for packet forwarding enable it.
Edit /etc/sysctl.conf and set net.ipv4.ip_forward = 1 TestingStart strongswan.
Check /var/log/messages and /var/log/secure for any errors. Ipad configuration
Set the Fields
A VPN connection should now be possible by toggling VPN to ON under Settings > VPN . |