|
一、前言 二、环境 三、基本配置 1.搭建LAMP环境 2.安装WordPress 3.安装phpMyAdmin 四、安全配置 1.身份验证 2.来源控制 3.加密访问(https) 五、测试 -------------------------------------------
一、前言 LAMP即Linux+Apache+Mysql+PHP,一组常用来搭建动态网站或者服务器的开源软件,本身都是各自独立的程序,但是因为常被放在一起使用,拥有了越来越高的兼容度,共同组成了一个强大的Web应用程序平台。随着开源潮流的蓬勃发展,开放源代码的LAMP已经与J2EE和.Net商业软件形成三足鼎立之势,并且该软件开发的项目在软件方面的投资成本较低,因此受到整个IT界的关注。从网站的流量上来说,70%以上的访问流量是LAMP来提供的,LAMP是最强大的网站解决方案. WordPress是一种使用PHP语言开发的博客平台,用户可以在支持PHP和MySQL 数据库的服务器上架设属于自己的网站。也可以把 WordPress 当作一个内容管理系统(CMS)来使用。WordPress 是一个免费的开源项目,在GNU通用公共许可证下授权发布。WordPress 被认为是Michel Valdrighi所开发的网志平台b2/cafelog的正式继承者。“WordPress”这个名字出自 Christine Selleck 的主意,他是主要开发者Matt Mullenweg的朋友。 phpMyAdmin 是一个以PHP为基础,以Web-Base方式架构在网站主机上的MySQL的数据库管理工具,让管理者可用Web接口管理MySQL数据库。借由此Web接口可以成为一个简易方式输入繁杂SQL语法的较佳途径,尤其要处理大量资料的汇入及汇出更为方便。其中一个更大的优势在于由于phpMyaAdmin跟其他PHP程式一样在网页服务器上执行,但是您可以在任何地方使用这些程式产生的HTML页面,也就是于远端管理MySQL数据库,方便的建立、修改、删除数据库及资料表。也可借由phpMyAdmin建立常用的php语法,方便编写网页时所需要的sql语法正确性。 二、环境 系统:redhat6.5 32位 IP:192.168.2.200/24 软件包: wordpress-3.9-zh_CN.zip wordpress主文件 phpMyAdmin-4.1.5-all-languages.zip phpMyAdmin主文件 三、基本配置 1.搭建LAMP环境
2.安装WordPress
将下面IP和域名写入hosts文件C:\Windows\System32\drivers\etc\hosts 192.168.2.10 www.yinuo.com 客户端浏览器访问 http://www.yinuo.com/wordpress/
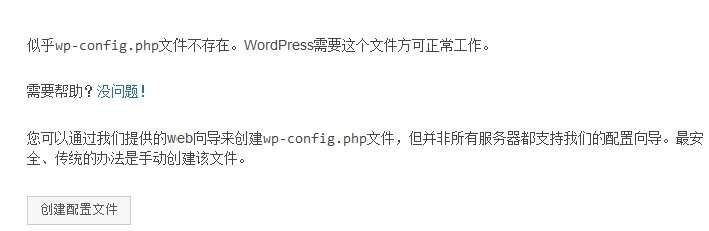
(1)点击创建配置文件。
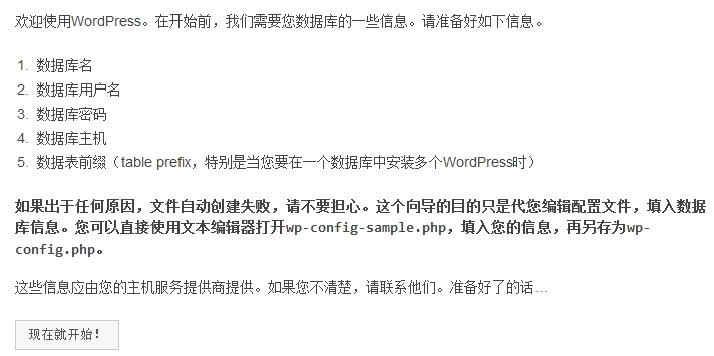
(2)点击现在就开始。
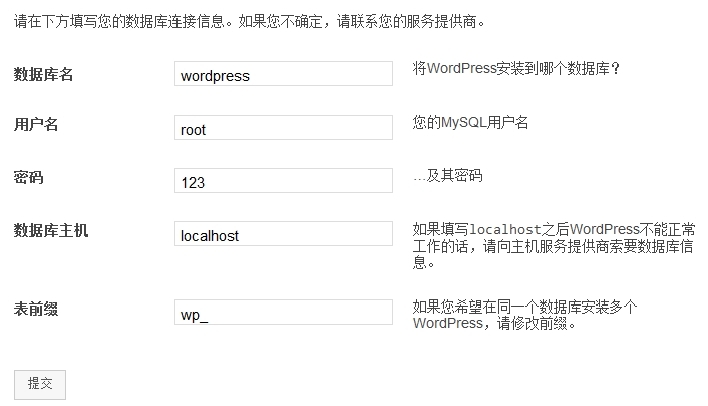
(3)写入用户名和密码,点击提交。
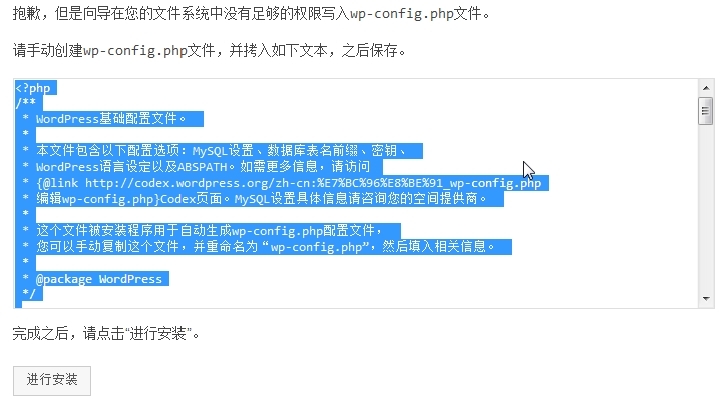
(4)按照提示,手动创建wp-config.php文件,并把文本复制进去,然后进行安装。
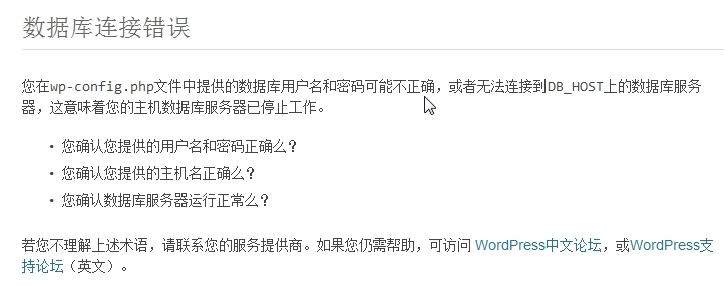
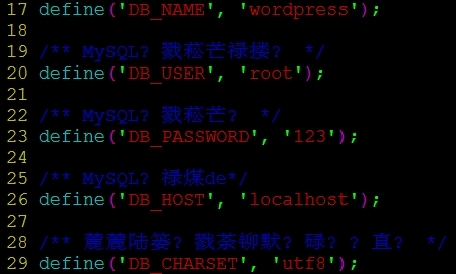
(5)如果数据库连接错误,一定要看下wp-config.php文件的17-26行,不许有任何错误(如下图)。
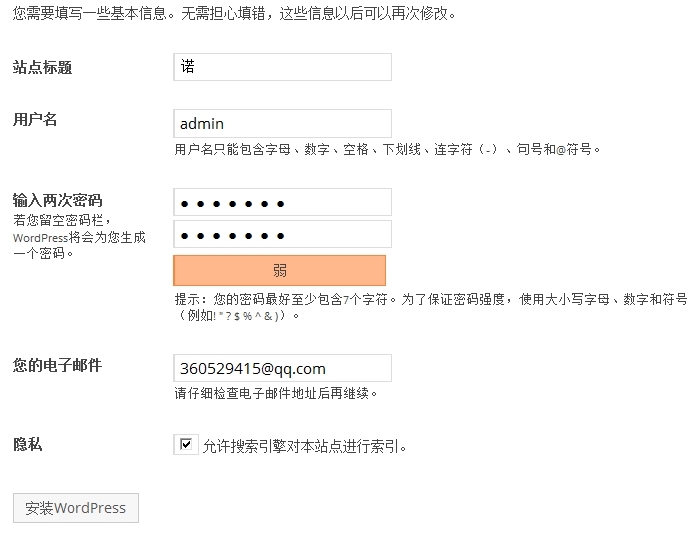
(6)填写站点信息,安装wordpress。
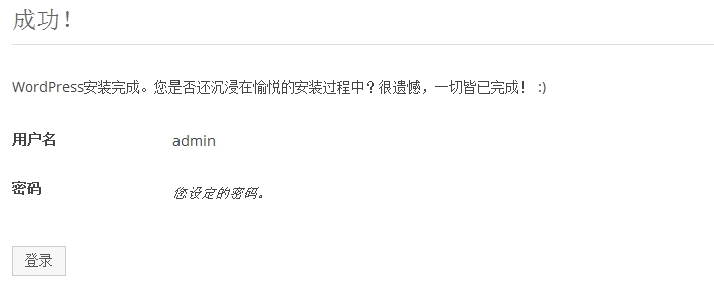
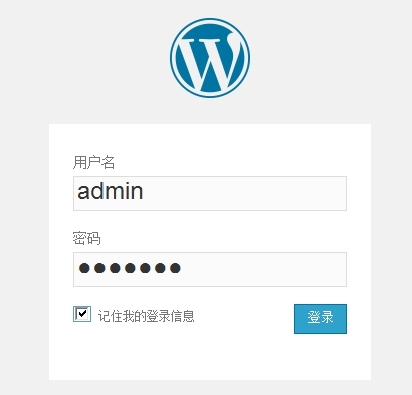
(7)已成功,可以进行登录了。
(8)登录测试。
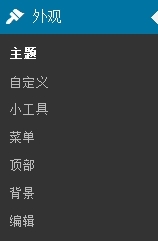
(9)更换个性主题,如fengying.zip。
3.安装phpMyAdmin
访问http://192.168.2.10/phpmyadmin/
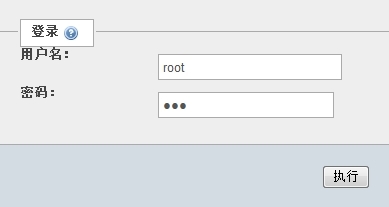
输入数据库的账号和密码。
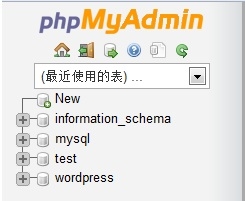
管理数据库(图形界面下的mysql管理工具)。
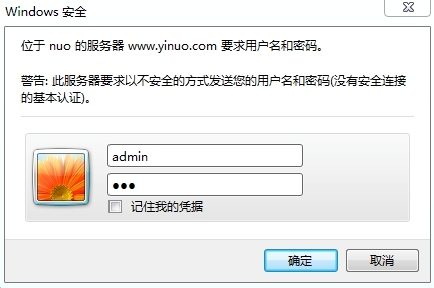
四、安全配置 1.身份验证
客户端浏览器访问 http://www.yinuo.com/wordpress/
需账号和密码才能正常访问个人主页。
2.来源控制
X.X.X.X 表示拒绝访问的IP。 3.加密访问(https)
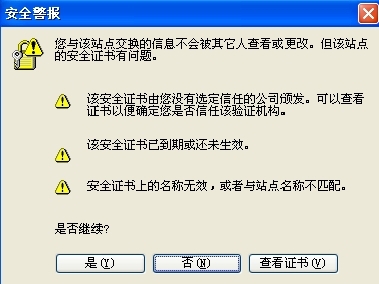
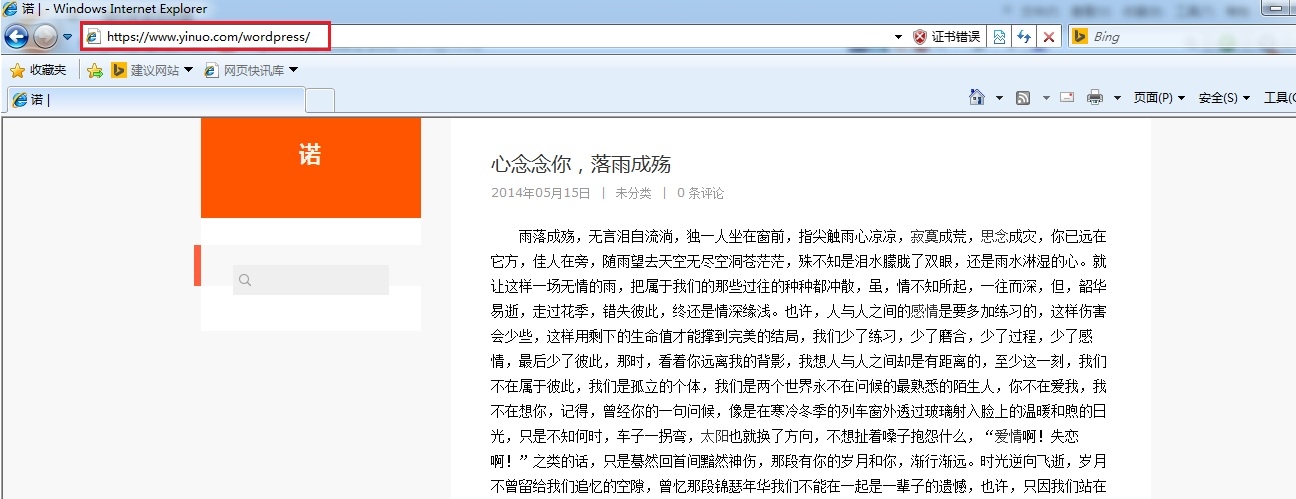
五、测试 客户端浏览器访问 https://www.yinuo.com/wordpress/
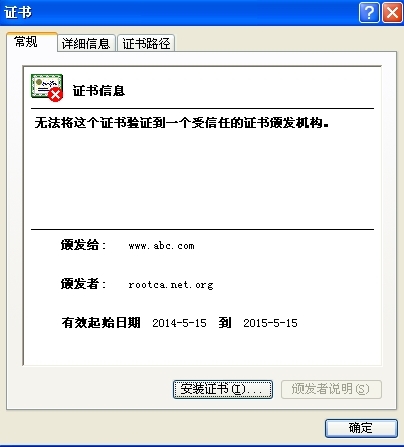
查看证书并安装。
主页展示
本文出自 “一诺千金” 博客,请务必保留此出处http://yinuoqianjin.blog.51cto.com/8360868/1352804 (责任编辑:IT) |