|
系统:CentOS Linux release 7.0.1406 (Core) 首先,设置系统语言格式,用系统自带的yum命令安装、升级所需的程序库 #LANG=C yuminstall gcc gcc-c++ libtool libtool-libs kernel kernel-devel libjpeglibjpeg-devel libpng libpng-devel libtiff libtiff-devel gettext gettext-devellibxml2 libxml2-devel zlib-devel net-snmp file glib2 glib2-devel bzip2 diff*openldap-devel bzip2-devel ncurses* curl e2fsprogs e2fsprogs-devel krb5krb5-devel libidn libidn-devel openssl openssl-devel vim-minimal unzip freetypefreetype-devel png jpeg zlib gd php-gd* libiconv libevent mhash mcryptyum-fastestmirror ntp patch flex bison tar pcre pcre-devel pcre-static automakeautoconf glibc glibc-devel openldap nss_ldap openldap-clients openldap-serverslibart_lgpl-devel pixman pixman-devel pango-devel* cairo-devel* perl-*curl-devel make apr* keyutils keyutils-libs-devel kernel-headers compat* mpfrcpp libgomp libstdc++-devel ppl cloog-ppl libcom_err-devel libsepol-devellibselinux-devel libXpm* php-common 一、安装前系统设置 1、修改当前的最大打开文件数 echo -e "ulimit -SHn 51200" >> /etc/rc.local echo -e "ulimit -SHn 51200" >> /etc/profile echo -e "* soft nofile 51200" >> /etc/security/limits.conf echo -e "* hard nofile 51200" >> /etc/security/limits.conf source /etc/profile 2、防火墙设置
centos7.0默认防火墙为firewalld(为了测试,关闭默认防火墙,使用iptables防火墙)
systemctl stop firewalld.service #停止firewall systemctl disable firewalld.service #禁止firewall开机启动 查看默认防火墙状态: firewall-cmd --state not running
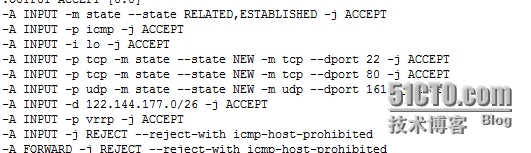
vi /etc/sysconfig/iptables
/bin/systemctl enableiptables.service /bin/systemctl restartiptables.service 3、修改selinux sed -i 's/SELINUX=enforcing/#SELINUX=enforcing/'/etc/selinux/config sed -i 's/SELINUXTYPE=targeted/#SELINUXTYPE=targeted/'/etc/selinux/config echo -e "SELINUX=disabled" >>/etc/selinux/config
4、卸载java包 rpm -qa | grep java (查询出来的java包都卸载) 5.重启reboot
二、安装lvs 122.144.166.21:LVS_MASTER 122.144.166.22:LVS_BACKUP 122.144.177.21:LVS_MASTER_VIP real_server:122.144.166.100 real_server:122.144.166.101
安装所需依赖包 yum install popt-static kernel-devel make gcc openssl-devel lftplibnl* popt* openssl-devel lftplibnl* popt* libnl* libpopt* gcc*
1、lvs安装部署:在两台LVS Server上安装lvs、keepalived软件(LVS_MASTER & LVS_BACKUP)
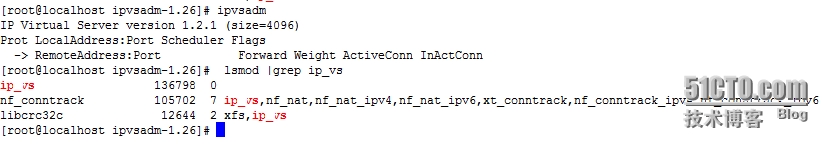
查看内核模块是否支持 rpm -qa | grep kernel-devel(默认已经安装) make && make install
加载ip_vs模块
3、keepalived安装部署: wget http://www.keepalived.org/software/keepalived-1.2.16.tar.gz tar -zxvf keepalived-1.2.16.tar.gz cd keepalived-1.2.16/ ./configure make && make install
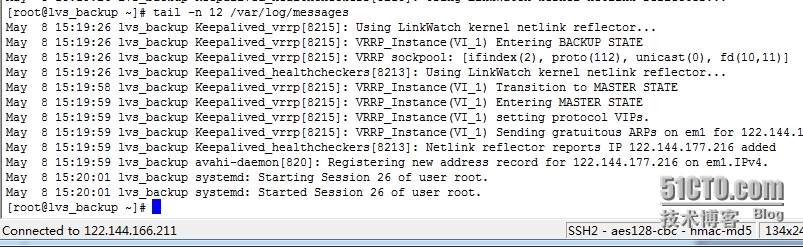
######### 将keepalived做成启动服务,方便管理########## cp /usr/local/etc/rc.d/init.d/keepalived /etc/init.d/ cp /usr/local/etc/sysconfig/keepalived /etc/sysconfig/ mkdir /etc/keepalived/ cp /usr/local/etc/keepalived/keepalived.conf /etc/keepalived/ cp /usr/local/sbin/keepalived /usr/sbin/ service keepalived restart 4、开启路由转发 vi /etc/sysctl.conf net.ipv4.ip_forward = 1 net.ipv4.conf.lo.arp_ignore = 0 net.ipv4.conf.lo.arp_announce = 0 net.ipv4.conf.all.arp_ignore = 0 net.ipv4.conf.all.arp_announce = 0 刷新系统变量,使系统文件变更马上生效 sysctl –p echo 1> /proc/sys/net/ipv4/ip_forward 5、在LVS_MASTER上配置虚拟vip地址 ifconfig lo:0 122.144.177.21 netmask 255.255.255.192 broadcast 122.144.177.255(我这里使用122.144.177.21为漂移地址,建议增加lo:0配置文件,为防止重启失效) 6、配置Keepalived ################个例详细介绍######################### vi /etc/keepalived/keepalived.conf ! Configuration File for keepalived global_defs { router_idLVS_DEVEL_MASTER #表示运行keepalived服务器的一个标识。发邮件时显示在邮件主题的信息 } vrrp_instance VI_1 { state MASTER #指定keepalived的角色,MASTER表示此主机是主服务器,BACKUP表示此主机是备用服务器 interface em1 #指定HA监测网络的接口 virtual_router_id 51 #虚拟路由标识,这个标识是一个数字,同一个vrrp实例使用唯一的标识。即同一vrrp_instance下,MASTER和BACKUP必须是一致的 priority 100 #定义优先级,数字越大,优先级越高,在同一个vrrp_instance下,MASTER的优先级必须大于BACKUP的优先级 advert_int 1 #设定MASTER与BACKUP负载均衡器之间同步检查的时间间隔,单位是秒 authentication {#设置验证类型和密码 auth_type PASS #设置验证类型,主要有PASS和AH两种 auth_pass 1111 #设置验证密码,在同一个vrrp_instance下,MASTER与BACKUP必须使用相同的密码才能正常通信 } virtual_ipaddress {#设置虚拟IP地址,可以设置多个虚拟IP地址,每行一个 122.144.177.216 } } virtual_server 122.144.177.216 80 {#设置虚拟服务器,需要指定虚拟IP地址和服务端口,IP与端口之间用空格隔开 delay_loop 6 #设置运行情况检查时间,单位是秒 lb_algo rr #设置负载调度算法,这里设置为rr,即轮询算法 lb_kind DR #设置LVS实现负载均衡的机制,有NAT、TUN、DR三个模式可选 nat_mask 255.255.255.0 persistence_timeout 50#会话保持时间,单位是秒。这个选项对动态网页是非常有用的,为集群系统中的session共享提供了一个很好的解决方案。#有了这个会话保持功能,用户的请求会被一直分发到某个服务节点,直到超过这个会话的保持时间。#需要注意的是,这个会话保持时间是最大无响应超时时间,也就是说,用户在操作动态页面时,如果50秒内没有执行任何操作, #那么接下来的操作会被分发到另外的节点,但是如果用户一直在操作动态页面,则不受50秒的时间限制 protocol TCP #指定转发协议类型,有TCP和UDP两种 real_server122.144.166.213 80 {#配置服务节点1,需要指定realserver的真实IP地址和端口,IP与端口之间用空格隔开 weight 1 #配置服务节点的权值,权值大小用数字表示,数字越大,权值越高,设置权值大小可以为不同性能的服务器,#分配不同的负载,可以为性能高的服务器设置较高的权值,而为性能较低的服务器设置相对较低的权值,这样才能合理地利用和分配系统资源 connect_timeout 3 #表示3秒无响应超时 nb_get_retry 3#表示重试次数 delay_before_retry 3 #表示重试间隔 } real_server 122.144.166.214 80 { weight 1 connect_timeout 3 nb_get_retry 3 delay_before_retry 3 } } ######################LVS_MASTER#################### ! Configuration File for keepalived global_defs { router_id LVS_DEVEL_MASTER } vrrp_instance VI_1 { state MASTER interface em1 virtual_router_id 51 priority 100 advert_int 1 authentication { auth_type PASS auth_pass 1111 } virtual_ipaddress { 122.144.177.21 } } virtual_server 122.144.177.21 80 { delay_loop 6 lb_algo rr lb_kind DR persistence_timeout 50 protocol TCP real_server 122.144.166.100 80 { weight 1 connect_timeout 3 nb_get_retry 3 delay_before_retry 3 } real_server 122.144.166.101 80 { weight 1 connect_timeout 3 nb_get_retry 3 delay_before_retry 3 } } ###################### LVS_BACKUP #################### ! Configuration File for keepalived global_defs { router_id LVS_DEVEL_BACKUP } vrrp_instance VI_1 { state BACKUP interface em1 virtual_router_id 51 priority 90 advert_int 1 authentication { auth_type PASS auth_pass 1111 } virtual_ipaddress { 122.144.177.21 } } virtual_server 122.144.177.21 80 { delay_loop 6 lb_algo rr lb_kind DR persistence_timeout 50 protocol TCP real_server 122.144.166.100 80 { weight 1 connect_timeout3 nb_get_retry 3 delay_before_retry 3 } real_server 122.144.166.101 80 { weight 1 connect_timeout 3 nb_get_retry 3 delay_before_retry 3 } } ################################################ 配置keepalived自启动 chkconfig --level 0123456 keepalived on 查看自启动状态 chkconfig --list keepalived 主备开启keepalived服务service keepalived restart ################################################ 7.测试####高可用性测试#### 模拟故障,将CentOS-LVS_MASTER上的keepalived服务停掉,然后观察CentOS-LVS_BACKUP上的日志,信息如下
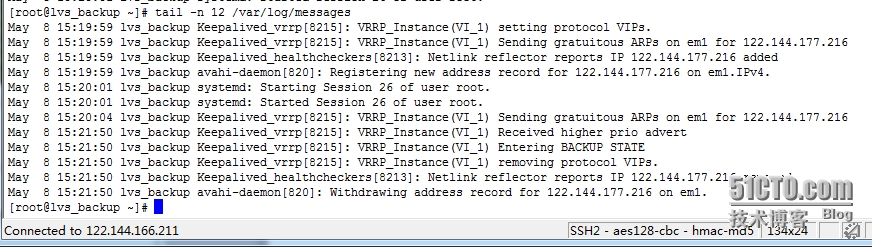
从日志中可知,主机出现故障后,备机立刻检测到,此时备机变为MASTER角色,并且接管了主机的虚拟IP资源,最后将虚拟IP绑定在em1设备上 将CentOS-LVS_MASTER 上的keepalived服务开启后,CentOS-LVS_BACKUP的日志状态
从日志可知,备机在检测到主机重新恢复正常后,释放了虚拟IP资源重新成为BACKUP角色. ############################################ Web服务器设置(122.144.166.100、122.144.166.101) ########################################### 在WEB1和WEB2机器上编辑如下文件 vi /home/shell/lvs_real.sh #!/bin/bash # description: Config realserver #Written by :http://kerry.blog.51cto.com SNS_VIP=122.144.177.21 /etc/rc.d/init.d/functions case "$1" in start) /sbin/ifconfig lo:0 $SNS_VIP netmask255.255.255.0 broadcast $SNS_VIP /sbin/route add -host $SNS_VIP dev lo:0 echo "1" >/proc/sys/net/ipv4/conf/lo/arp_ignore echo "2">/proc/sys/net/ipv4/conf/lo/arp_announce echo "1">/proc/sys/net/ipv4/conf/all/arp_ignore echo "2">/proc/sys/net/ipv4/conf/all/arp_announce sysctl -p >/dev/null 2>&1 echo "RealServer Start OK" ;; stop) /sbin/ifconfig lo:0 down /sbin/route del $SNS_VIP >/dev/null2>&1 echo "0">/proc/sys/net/ipv4/conf/lo/arp_ignore echo "0">/proc/sys/net/ipv4/conf/lo/arp_announce echo "0">/proc/sys/net/ipv4/conf/all/arp_ignore echo "0">/proc/sys/net/ipv4/conf/all/arp_announce echo "RealServer Stoped" ;; *) echo "Usage: $0 {start|stop}" exit 1 esac exit 0 ############################################## 赋给执行权限 chmod 777 /home/shell/lvs_real.sh chmod 755 /etc/rc.d/init.d/functions 别人的配置文档中没这个步骤,我不知道为什么总是说执行到这句时没有权限,所以我添加了执行权限 chmod 755 /home/shell/lvs_real.sh /home/shell/lvs_real.sh start (责任编辑:IT) |